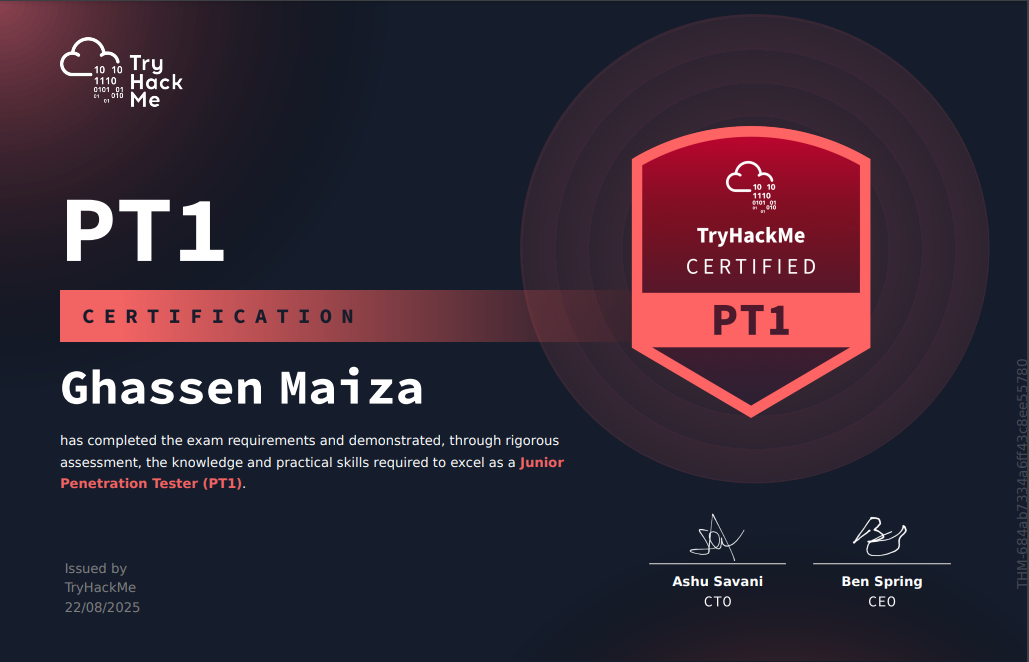
Introduction & How I got the certification
Last week I passed the new Junior Pentester certification, PT1 from tryhackme. The PT1 is hands-on experience certification where a candidate must prove his skills in multiple categories (Web Exploitation, Network and Active Directory) by taking a 48 hour exam.
The PT1 cert is priced at 297$, while the comparaison on their website, they compare it with certs like pentest+ and CEH (probably to make it look cheaper). I think it should be compared to similar junior hands-ons certs as the others are theoretical MCQ exams :
| Cert | Price |
|---|---|
eJPT | 249$ |
PJPT | 249$ |
PT1 | 297$ |
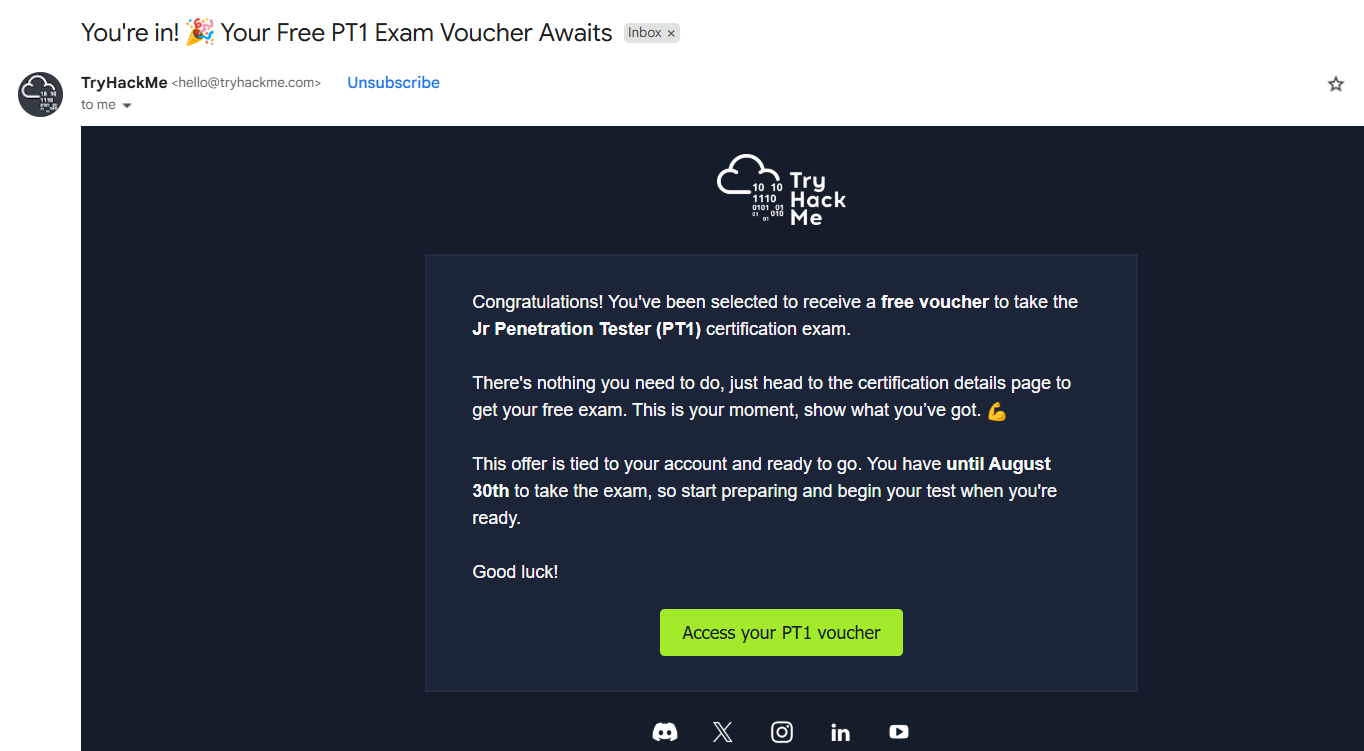
While higher then the others I think it’s still reasonable, will dive into comparing those certs later. Lucky me I didn’t have to pay for the cert since they posted a voucher giveway for those who have OSCP, PJPT or eJPT when they first launched the cert, I took my chance and got an email that I got offerd a free voucher to take the cert :
Prior to PT1
Prior to taking the PT1, I had already took the PJPT (Practical Junior Penetration Tester) from TCM-Security,you can checkout my PJPT review, also I got other Microsoft certs but honestly for me if a cert isn’t practical and hands-on it dosen’t count. I also used to play TryHackme rooms and paths when I first started the InfoSec journey, but now I play HackTheBox (When I get the time tosince I’m doing an apprentice program so I’m either working or studying) I’ve also played multiple CTFs competitions (I’ve lost count xD), shout out to pwn.spawn() my team.
Anyways so you get it I’m not totally new to the field, so my experience might be a little diffrent from others.
Course & Preparation
While TryhackMe don’t offer a specific course for the certification, the do offer a reccomended learning that is based on their platform learning paths like the Jr Pentester, Web Fundamentals and in addition to practical rooms which are basically machines with varying difficulty for the candidate to pwn :
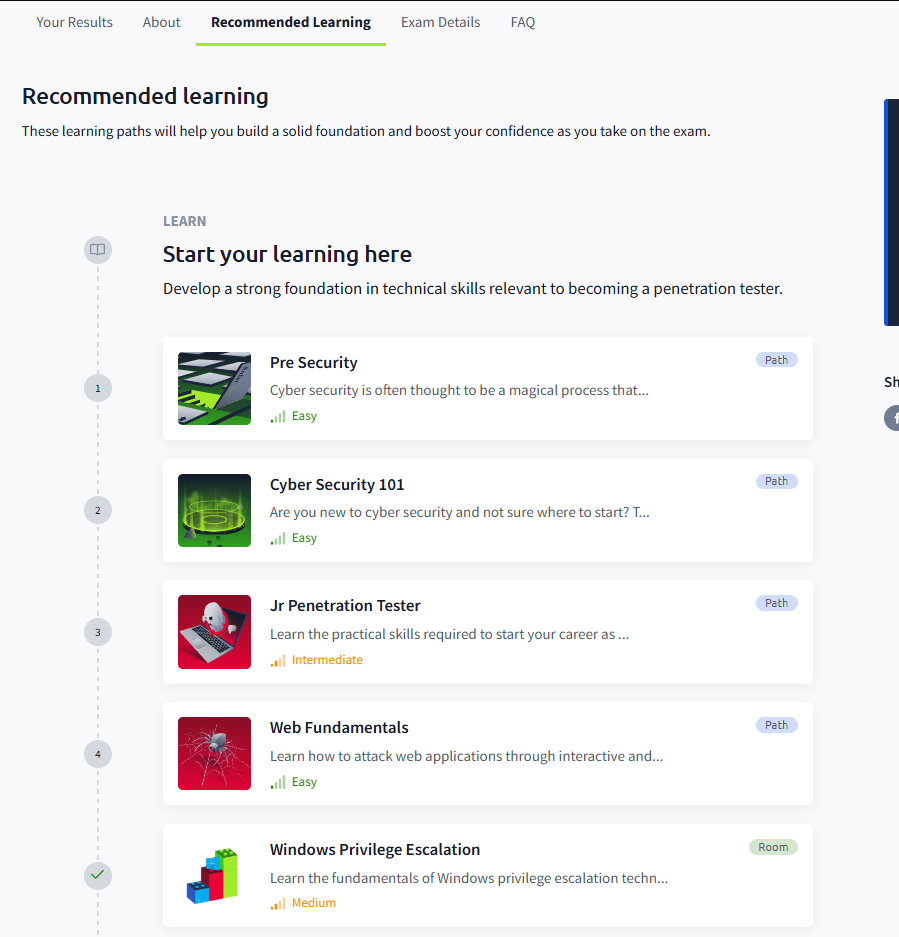
For me since I used to play on thm, I already have done a lot of these paths in the past, however I quickly went back and did a speedrun on some of the modules in order to make notes for the exam, because I’ve read other reviews saying that If you don’t prepare for the exam or If you underestimate it you will get a slap in the face while taking it.
I even saw people with certs like CRTP, OSCP say that you shouldn’t take the exam without prep and “It’s not as junior as you think”. So I focused on the AD learning and some Web Exploitation parts and the Windows Privesc module.
For note taking I used Notion, to take some notes for either commands (for the AD portion) or checklists (For the Web part), here is my notes structure :
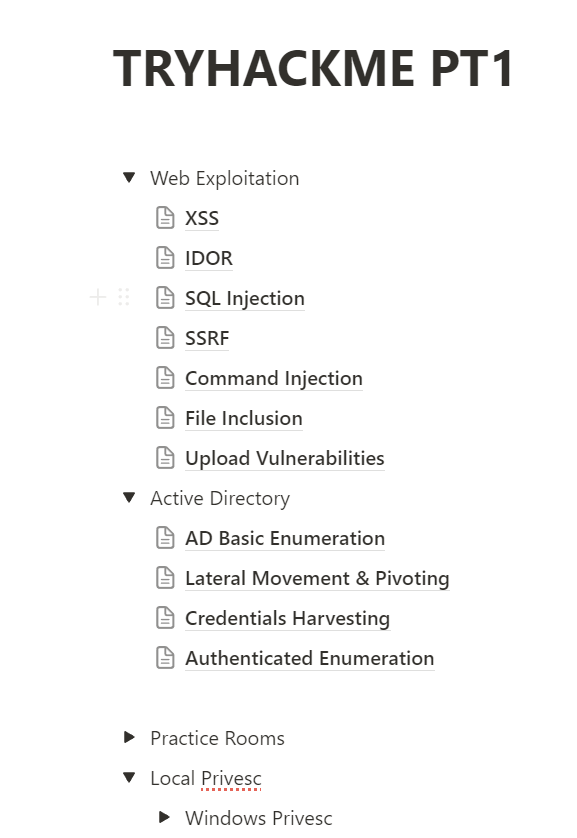
Here is my approach to taking notes in this cert for the Active Directory part you need to take detailed notes of the commands and tools to use in each phase (Enumeration, Exploitation…etc.) that saves the time in the exam to keep looking for the right syntax to each command.
However I didn’t do that for the Web Exploitation Portion since web application vulns and exploits are very specific to the context, you can’t just copy-pasta a payload and expect It to work, Instead I did a checklist of things I should check for for each vulnerability, let’s take SSRF as an Example here is what a checklist would look like :
- Identify all points where the application makes a server-side HTTP request ☐ - URL parameters - Form fields - HTTP headers- Examine the application's handling of URL redirection ☐- Test different URI schemes http, https, file, ftp, etc. ☐- Does the application accept IP addresses (e.g., 127.0.0.1) or localhost as the hostname? ☐- Test for internal network interactions ☐- Can you map out the internal network infrastructure (port scanning, banner grabbing)? ☐- Test for remote file inclusion ☐- Test for cloud metadata exposure (relevant for cloud-based services) Amazon AWS, Google Cloud, etc. ☐- Is there a blocklist? ☐- Can you bypass the blocklist? ☐- Encoding Hostname obfuscation ☐- Alternative IP notation (e.g. 127.0.0.1 in hex is 0x7f.0x0.0x0.0x1) ☐- Hex, Hex with extra 0s, Octal, two numbers, three numbers, etc ☐TIPFor this I highly reccomend Alex Olsen’s AKA AppsecExp checklists that you can find on his Appsec Explained website.
The Exam
The exam is 48 hours of exploiting and crafting a report of the findings. In order to pass the exam a candidate must score a minimum of 750/1000, the exam consists of 3 portions :
- Web Application Pentest: 400 points (4 Flags)
- Network Pentest: 360 points (2 machines, 4 Flags)
- Active Directory Pentest: 240 points (2 Flags)
For each section you are provided with Rules Of Engagement, Summary and Scope that makes it feel like a real pentest. I settled for the exam on a tuesday at about 12pm, and having read reviews about how hard the web exploitation part is I chose to first tackle the Network and Active Directory portions so when I get to the Web part there’s less pressure on me.
Network Pentest portion
This was a walk In the park you Have 2 Boot2Root machines (Linux and Windows) where you have to get a user and root/system flag on each one of them, and honestly for someone who has played THM,HTB this is a straight forward boxes, I’d say It’s the equivalent of an easy THM Box or even a Very Easy HTB machines.
I can’t dive into further details since I am not allowed to talk about the exam but for this part I don’t think anyone will struggle. I personally finished the 2 Boxes in around 1 hour but then I came back and pwnd the Linux box in a second method and took detailed notes and screenshots (will talk more about the screenshots in the reporting phase xD). It was already 2pm so I got lunch and then came back at 3pm to tackle the Active Directory portion
Active Directory portion
For this portion we have a user Domain joined machine and a Domain Controller, so we have to fully compromise the domain and get 2 flags. I started enumerating and got access to the user machine about 15 minutes in, honestly the initial access didn’t feel realistic at all from my experience, It was so CTFy. At this point I thought that PT1 is overrated and I can finish the exam in a matter of couple hours and call it a day.
Moving forward to compromise the DC this where I struggled a bit and wasted about 2 hours in some rabbit-holes and I felt like I had no lead, I Enumerated again and knew the exact path to get to a Domain Admin but still the tools I used weren’t functionning right. After a frustration of about 1 hour I decided to change the tool and indeed the path that I had from enumerating was right and I just needed to change the tool. So It was a total 4 hours of getting from the User Workstation to the DC as Domain Admin. Now that I cleared both Network & AD I felt a bit of relief and went out with friends (shoutout to NDLx0 & K-Ha$h), and I didn’t get back to finish the Web portion until tomorrow.
Web Exploitation portion
Now comes the time that I was personally waiting for as I heard that the hype of the PT1 revolved around this section, and most of the videos and review say it’s not meant for a junior certification, do I agree ? well partially but you have to know that the vulnerabilities in the web part are auto-generated so its diffrent from an exam attempt to another.
So I started the web portion at about 12pm, I tried to explore the app since there was a lot of features and functionnalities so trying to get familiar with the app first (While having Burpsuite proxy capture the traffic), then going through the captured requests I noticed you would usually encounter in web challenges, especially if you have played web challenges in the past. That was about an hour in. In the next hour I found the same vulnerability in diffrent parts of the app, and I could exploit it however I couldn’t get the flag for it, I kept trying diffrent techniques over and over but still can’t grab the flag, while you get some credit points for found vulnerabilities without the flag it would be much less points than having the flag.
I decided to not get stuck with that vuln and moved forward, where I found the second vulnerability along with the flag and it was the same as a vulnerability in the provided practice rooms.
CAUTIONAt this point I thought that I passed the exam thinking that the points in each section are granted for the flags so I thought that I already had 800/1000, In reality each section points are awarded not only for the flag and but the reporting of the exploitation. So I advise everyone taking this cert to at least grab 9/10 flags to secure that you pass, below is an example of how rating works (the redacted parts are reporting part points).

By 4pm, I started digging for more vulnerabilities, I felt like I literally tried everything but nothing worked, so I stalled for about 4hours straight but everything lead to a dead-end. I thought I should end the exam there (since at that time I thought having 8 flags means I passed), but I decided to give another chance to the vulnerability that I found earlier but couldn’t get the flag for, more enumeration later and trying the vuln on other endpoints It worked and I got the flag for that exploited vuln, It was so easy to find but kinda hard to get the flag for it. At that point it was 8:30pm and decided to accept the 9/10 flags and start working on my report since I have to submit the day after before 12pm.
The Report
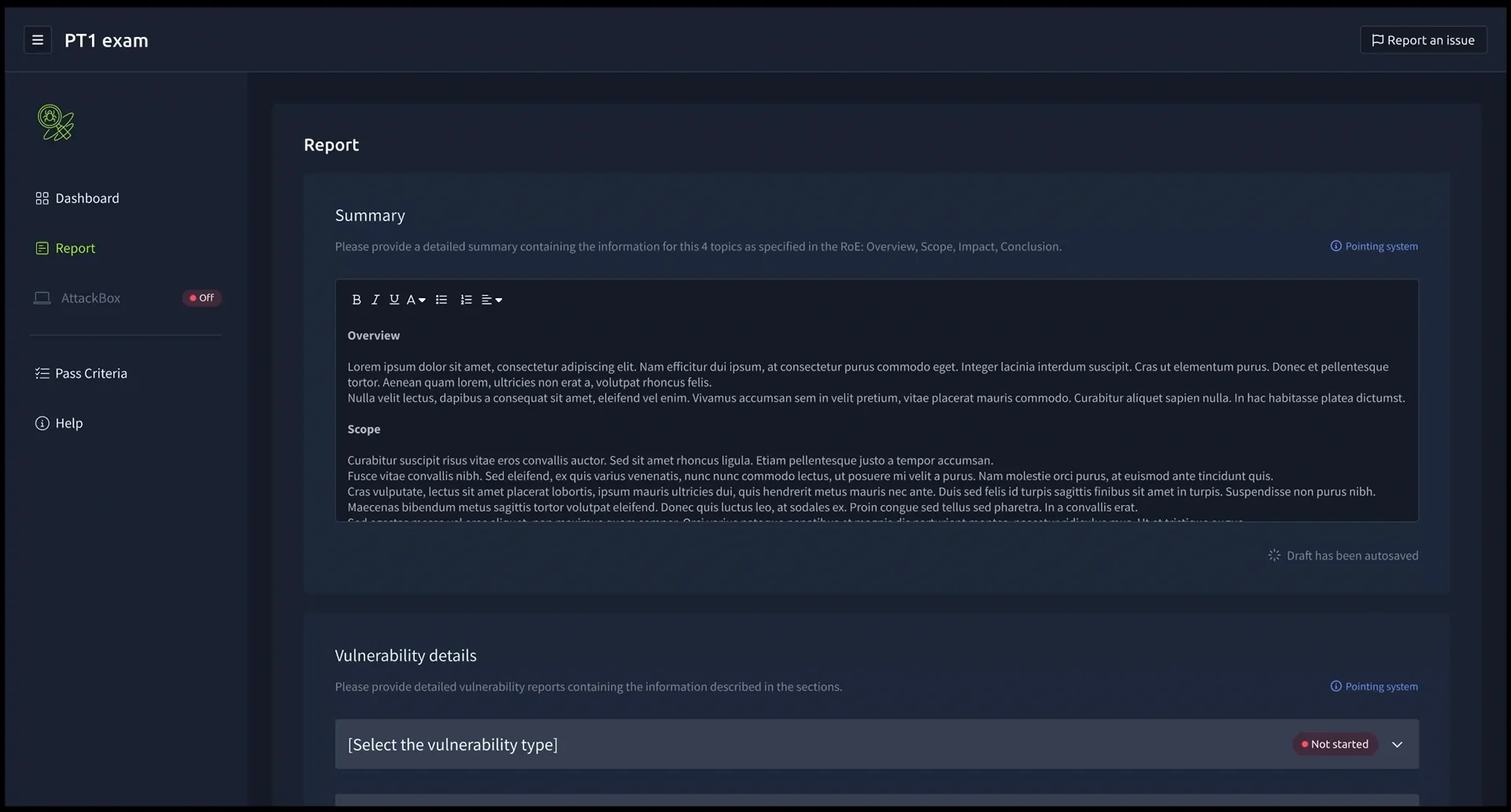 Tryhackme provides a reporting dashboard where you have to submit a report for each section of the Exam (Web Exploitation, Network and Active Directory). For each portion you have to do a Summary and then select the vulnerability type, its severity, Impact and remediations and it was all text based. Guess what ? I didn't know that prior to taking the exam, so my 999+ screenshots that I took went to waste but that's okay I had the commands and everything as well.
Tryhackme provides a reporting dashboard where you have to submit a report for each section of the Exam (Web Exploitation, Network and Active Directory). For each portion you have to do a Summary and then select the vulnerability type, its severity, Impact and remediations and it was all text based. Guess what ? I didn't know that prior to taking the exam, so my 999+ screenshots that I took went to waste but that's okay I had the commands and everything as well.BUT…BUT.. this didn’t seem realistic to me because In real pentest and assessments you would either do reporting from scratch or 90% of the time would have personal/organization template that you would follow, but this limits us to what we put in the report. Another thing after submission you can’t see the full report of the assessment, download it or whatsoever, I don’t know if they assemble each part after submission but you don’t get to see the full report.
I finished reporting all the sections and only thing left for me was to put all the flags in their section. I was excited to submit my exam attempt and get the certification, since they had an Ai that grades and give instant results. But this is when I ran into an Issue.
The Issue I faced
The flags for the Network portion aren’t accepted !! 4 flags !! It was expecting a specific format of a uuid, however the flags I got from completing the machines are hashes which showed an error message and didn’t allow me to finish the exam and submit my report. I emailed support at 9:15pm, but they were out of their working hours at that time. Tried to look for solutions on the tryhackme discord but didn’t find any, also another person on discord was having the same Issue as mine. Here is the Timeline for my Issue :
-
9:14pm : Emailed support about the error in the flag format
-
1:25am : Reply to the sent email saying that another discord member had the same issue and they told him to reset to fix but It didn’t
-
9:56am : Sen another reply to get an update on my issue
-
10:39am : sent a new Email with the same Issue and reference to the other email (at this point almost an hour to the exam submission)
-
Around 11 am : I texted the issue through the Tryhackme Bot where I got instant reply from support, they first said that the flags I have are incorrect but after providing screenshots (at least they were useful xD) they started investigating the issue and gave me an extension of 3 hours for my exam.
-
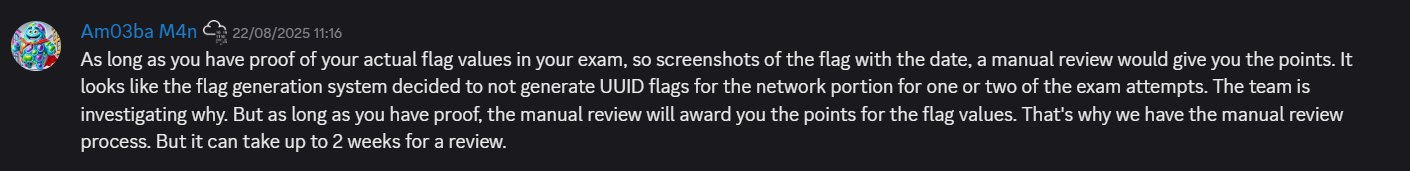
11:16 am: : On discord
-
12:03pm : The Issue was fixed so according to support either submit the old formats and might wait 2 weeks for manual review and to get my cert, or redo the network portion.
For sure I went back and quickly did the whole network portion to grab the new fixed flags and submit them. I get it its a new cert but tryhackme have been operating for years in this field, plus support weren’t very responsive especially via email, compared to TCM’s security support they respond instantly either via email or discord. Anyways after submitting I got instant results that I passed and got my cert 🎉.
Oh and by the way the Ai is very on point when giving strengths and areas of improvements for your report, cause I saw a lot of reviews and people who did not get the cert hating on the Ai grading saying its not accurate, from my experience it was very on point.
Comparaison & Final Thoughts
A lot of people who took and reviewed the PT1 say that the cert goes beyond what a junior pentester needs, I believe that the PT1 exam might be challenging for someone with no prior experience in cybersecurity but the skills learned and proved are a must have as a junior pentester, I think other certs like eJPT got their bar pretty low when it comes to the exam, so when people take a real junior pentester exam they think its way harder.
If you have no prior experience I highly advise anyone to start their journey doing TryHackme and HacktheBox and then for certs PJPT and PT1 are good starting points.
Overall PT1 is a great hands-on junior pentesting cert, but don’t underestimate it. It’s a solid addition to your certs, offers good practical experience, and is worth the effort.

