
SparkCTF 2k04 :
A detailed-writeup for some of the Mobile tasks that I solved during SparkCTF 2024 edition. I’ll go through how I approached the tasks, the steps I took, and what I learned along the way.
Task 1 - Androfire :
 Well for the first one right off the bat we should know what we will be loooking for since the title and the description are hints that the Mobile app is using Firebase as a database
which is so common for Mobile applications but let's dive deeper into it.
Well for the first one right off the bat we should know what we will be loooking for since the title and the description are hints that the Mobile app is using Firebase as a database
which is so common for Mobile applications but let's dive deeper into it. We are provided with an .apk file so first thing we need to do is to decompile it with tools such as (apktool,jadx,bytecodeviewer..etc) we will use apktool for this one :
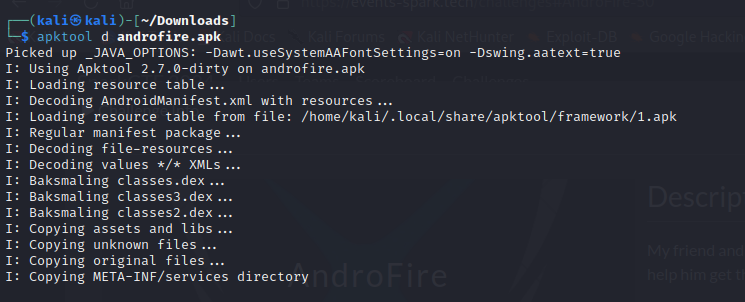
We will check the manifest file which describes essential information about the app and how components(Activities,Intents,Services…etc) interact with each other:
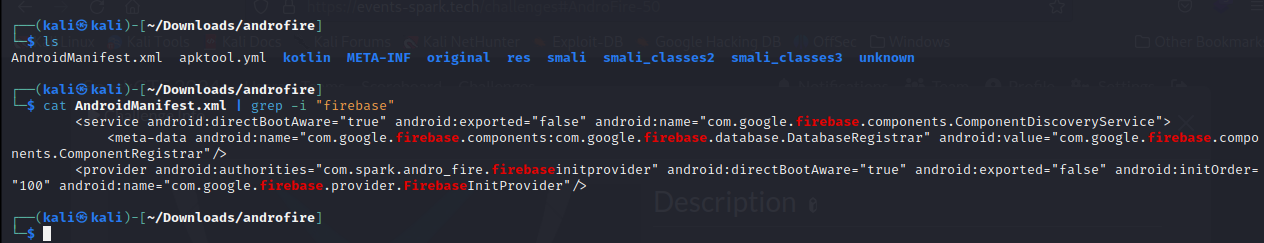 one of the services is a firebase database so first thing that comes to mind that we should look for the firebase url somewhere checking the
one of the services is a firebase database so first thing that comes to mind that we should look for the firebase url somewhere checking the /res/values/strings.xml we get the firebase url :
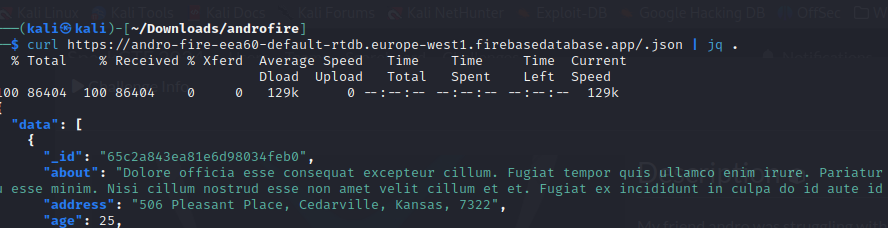
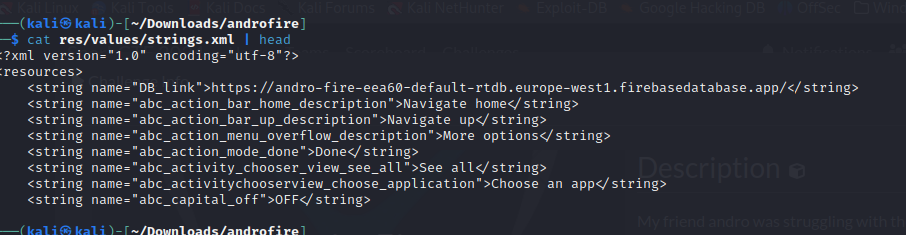 Now if the database is misconfigured and gives anyone read privileges we should be able to get it at
Now if the database is misconfigured and gives anyone read privileges we should be able to get it at /.json endpoint since all real time firebase database is stored as a json object :
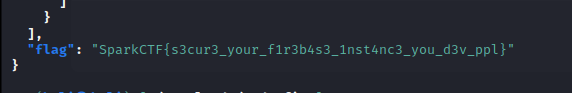
Flag 01 : SparkCTF{s3cur3_your_f1r3b4se_1nst4nc3_you_d3v_ppl}
Task 2 - Flag Dump :
 For this one looks like we need to dump the app memory first thing first let's just open the app and see the interface (I already have a preconfigured android VM that i will be installing the `.apk` file into) :
For this one looks like we need to dump the app memory first thing first let's just open the app and see the interface (I already have a preconfigured android VM that i will be installing the `.apk` file into) :
Nothing interesting it’s just displaying a text, let’s try to decompile the apk this time with jadx-gui for a better source code review :
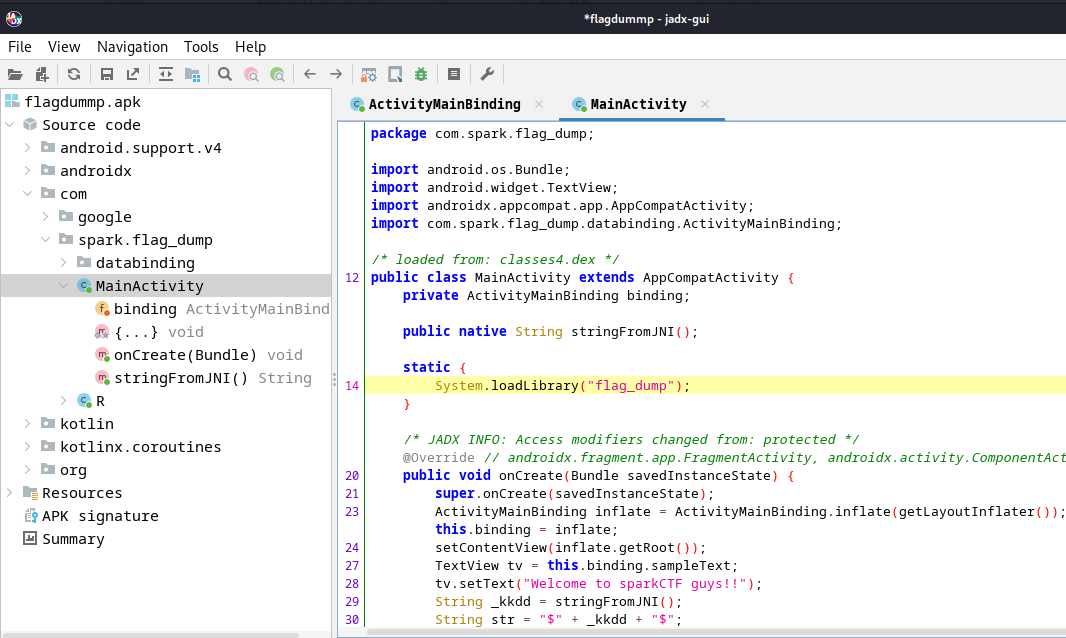 In the
In the MainActivity it’s loading a library called flag_dump let’s extract the library and decompile it using ghidra to try to undrestand the logic behind this :
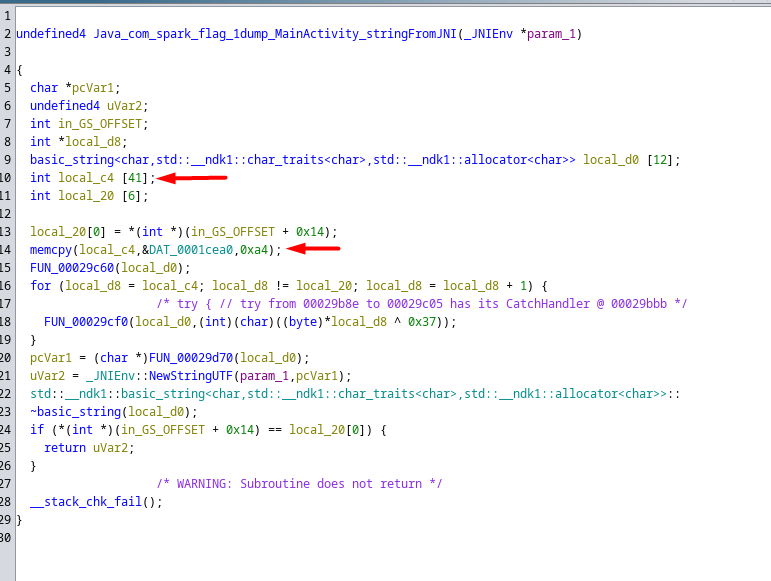
from the two highlighted lines we can see that it is loading local_c4 into memory starting from one particular address and storing 164 bytes, so there is probably something that is being moved from one memory location to another, let’s use adb (Android Debug Bridge) to connect and install our apk file :
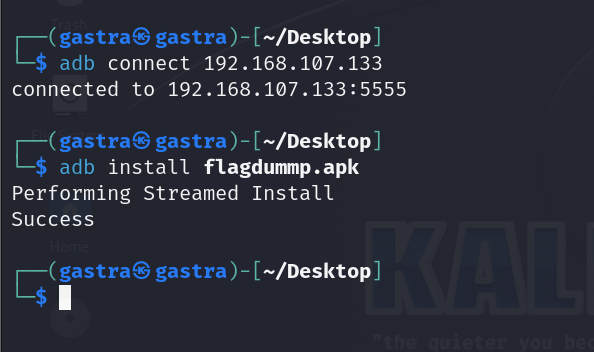 Now in order to dump the memory for our android app we will use
Now in order to dump the memory for our android app we will use frida which is a dynamic instrumentation toolkit
that is used for many things such as Read app memory,Hook methods/functions…etc for this we need to install Frida-Server on our android
by selecting the right image and also install the fridump on our attacker machine that will dump the memory for us.
On The Android Machine : We push the frida-server and grant it executable permissions.
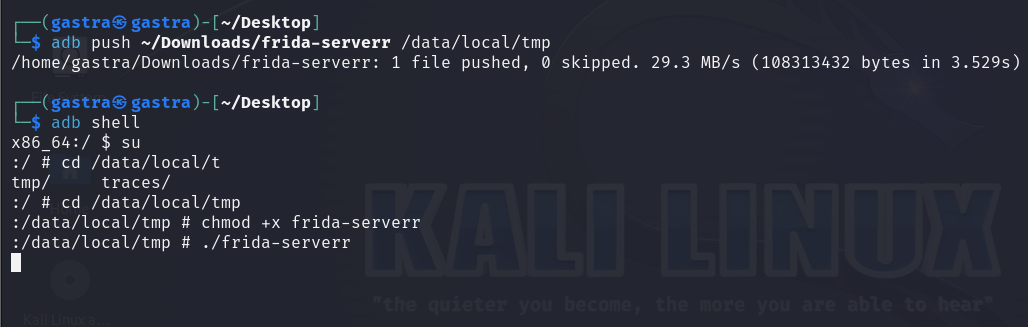
On The Attacker Machine :
First we display all the packages and then we pass as an argument for fridump our taget package which is flag-dump.
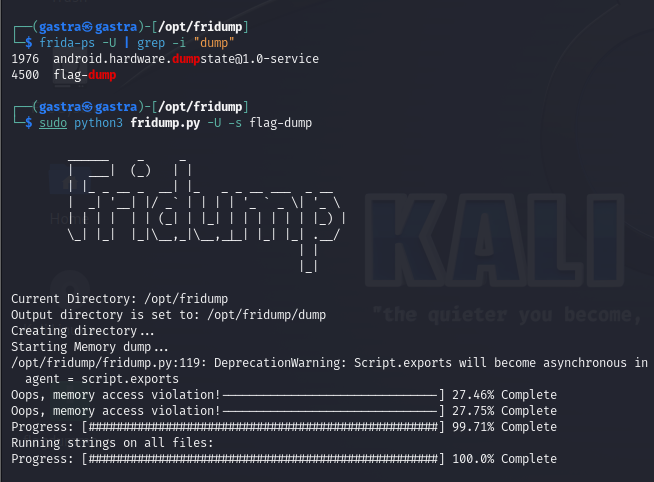 so the output is bunch of memory dumped data :
so the output is bunch of memory dumped data :
we won’t bother checking all of dumps the we already know what we are looking for :
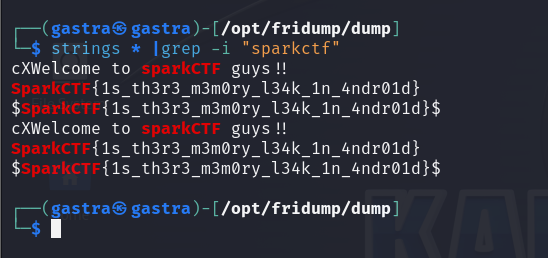
Flag 02 : SparkCTF{1s_th3r3_m3m0ry_l34k_1n_4ndr01d}}
Task 3 - Flag Checker :
For this one the author created a native Library that will check for the flag, So the first thing that should be done is to extract the library and try to undrestand the logic behind it,
before that i tried to go for a low hanging fruit by running MobSF On the apk file but nothing seems interesting, as usual let’s decompile the apk and check our MainActivity :
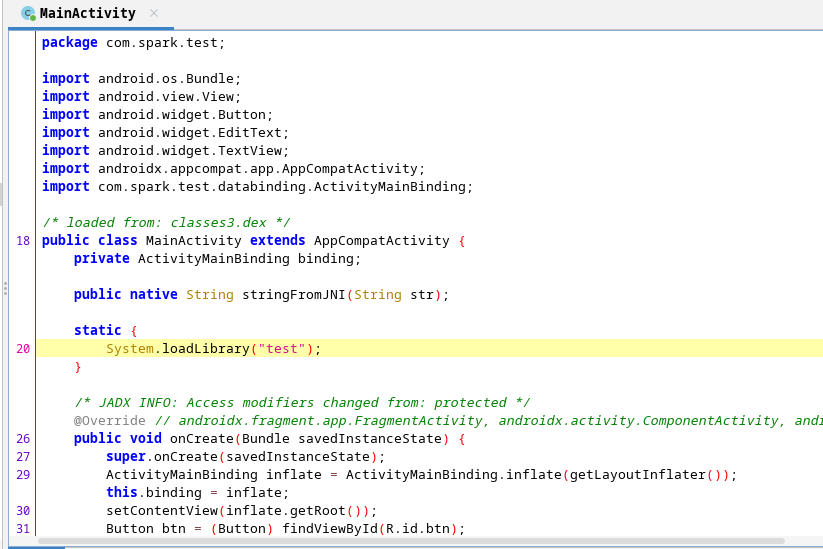 Indeed there is a
Indeed there is a test library that is being loaded let’s check it out in ghidra and do some reverse engineering :
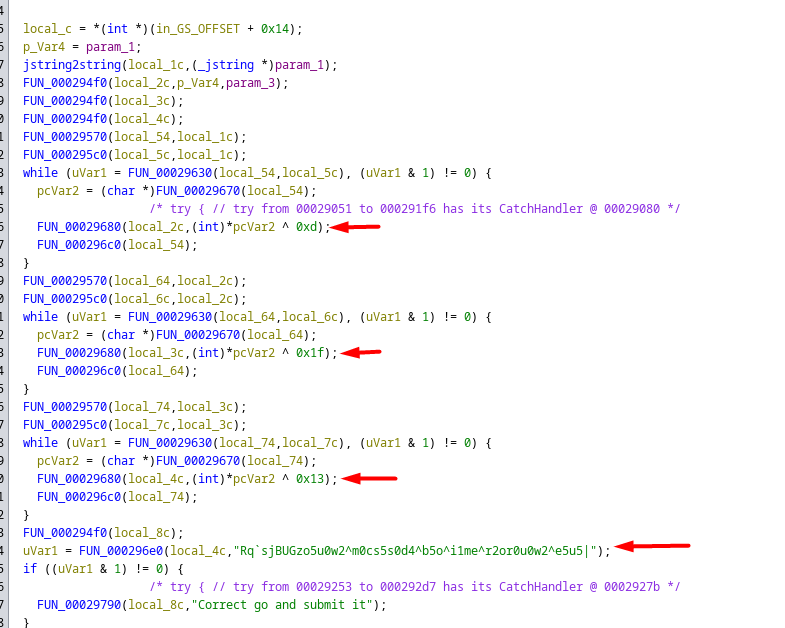
Upon checking the decompiled code it was quiet complex since there were too many functions calling each other but we will focus on the following one Java_com_spark_test_MainActivity_stringFromJNI
we notice one weird string, i dropped the decompiled code for chatgpt and asked for explanation and here’s what i got :
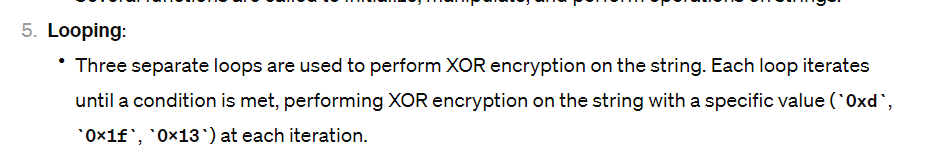
So it’s xoring the string three time first with 0xd (13), 0x1f (31) and 0x13(19), let’s write a small python script that will xor the string backward to it’s original state or we could simply use Cyberchef :
def xor_string(input_string, key): return ''.join(chr(ord(char) ^ key) for char in input_string)
x=[19,31,13]gibberish = "Rq`sjBUGzo5u0w2^m0cs5s0d4^b5o^i1me^r2or0u0w2^e5u5|"
for i in x: print(f'[*] Xoring With {i} : ',end="\t") dec=xor_string(gibberish,i) gibberish=dec print(dec)Output :
$ python3 solver.py[*] Xoring With 19 : Abs`yQFTi|&f#d!M~#p`&`#w'Mq&|Mz"~vMa!|a#f#d!Mv&f&o[*] Xoring With 31 : ^}lfNYKvc9y<{>Ra<o9<h8Rn9cRe=aiR~>c~<y<{>Ri9y9p[*] Xoring With 13 : SparkCTF{n4t1v3_l1br4r1e5_c4n_h0ld_s3ns1t1v3_d4t4}Flag 03 : SparkCTF{n4t1v3_l1br4r1e5_c4n_h0ld_s3ns1t1v3_d4t4}
Final Thoughts :
Since I was new to playing Mobile tasks this gave me a good way to practice some of the things i learned lately, It was a good experience even though I didn’t get the chance to enjoy the full experience by playing on-site, shoutout to @Codiac the author and to Engineer’s Spark Iset’com for another magnificent edition of SparkCTF.

